Yesterday, I used a new approach to more easily convert text into usable social networks that can be analyzed. I used Alice in Wonderland, so that I could compare to the approach that I used in my book.
I like to use fictional social networks to demonstrate network attack, so, today I’m going to do that. Today’s post will be different than usual.
I come from cybersecurity, and think in terms of offense and defense. There is a quote I heard while working at a previous job: "Defenders think in lists, attackers think in graph.”
I don’t agree with the quote, because I am showing you how you can think in graphs or networks. This is just heightened awareness. I call this heightened awareness Network Thinking.
I believe that network thinking is valuable because it presents opportunities to understand and influence the world around us. I’ve already written several posts about how this is useful for understanding. Today, I’m going to show a type of influence: disruption.
Obviously, there are other kinds of influence. We’ll talk about those another day. Today, we’re going on the offense. We’re going to pretend that the red queen got her way.
Network awareness can be useful for defense as well. If you understand your environment, you can bolster it so that it is less brittle. But if you think in terms of lists, not graphs, you will do things differently. We can do some defense experiments another day.
Disruption Approaches
You can get see today’s code here.
Today, I am going to try two different approaches to cause as much disruption to the Alice network as possible. The goal is to shatter the network into pieces so that communication is disrupted and the social group is broken into small pieces.
Approach 1 (Sequential): I will do four iterations, dropping the node with the highest betweenness centrality at each step. In each step, betweenness centrality is recalculated.
Approach 2 (Burst): I will simultaneously drop the four nodes that had the highest betweenness centrality scores in the original network.
My intuition is that the first approach will cause greater disruption, as the most important node is identified at each step. I expected that this would take more work but have more impact.
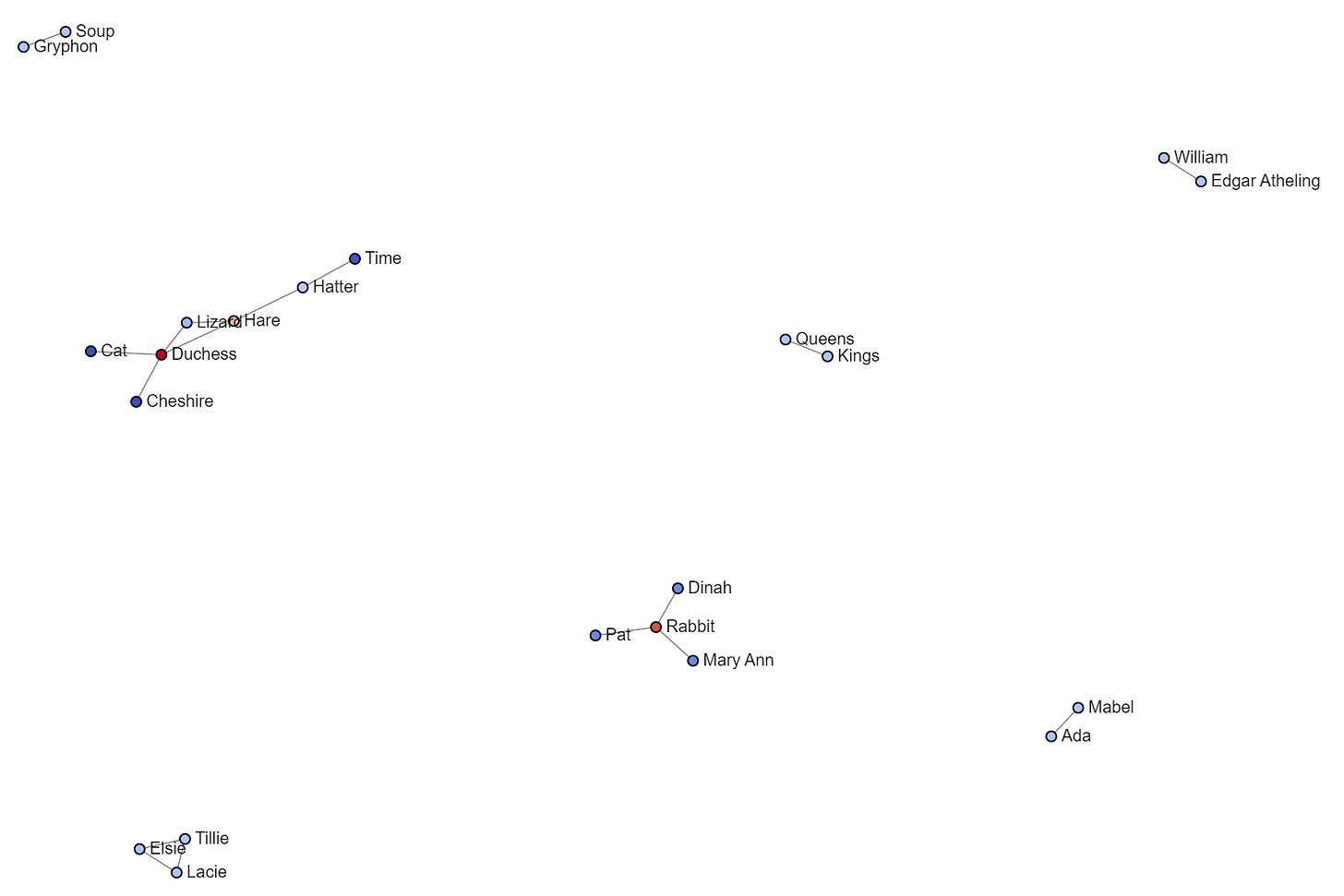
First, let’s look at the original network.
Even visually, you should be able to notice that if Alice’s node is removed, many nodes will become disconnected. Learn to notice weak spots in networks. They often look like stars.
Approach 1: Sequential
Please see the code, for more detail. I will show the results on this blog.
In the first iteration, Alice was removed.
I am not showing isolate nodes. Already, we can see that the network looks significantly different, and it has broken into pieces. What nodes do you think have highest betweenness centrality? Learn to notice them visually.
Next, Hatter is removed. The Mad Hatter!
Notice that the community that he was a part of has split.
Next, Rabbit is removed, the White Rabbit.
Finally, Duchess is removed.
And that is all that is left of the communication channels in this social network. The largest cluster only has five nodes.
Approach 2: Burst
In the second approach, I identified the four nodes with highest betweenness centrality, and then I dropped them all at once, in one burst. This was a simpler approach, so there is only one output image.
I can already see that this method appears less effective. Take a look at Hatter’s community on the left. Several important characters are still grouped together. This shattered the network, but in this instance, it looks a bit less effective. Key figures are still working together.
Approach Comparison
Let’s compare the two approaches.
Original Density: 0.075
Final Density:
Approach 1: 0.032
Approach 2: 0.032
Hmm, ok, this looks identical. Are they equally effective?
Original Connected Component Count: 1
Final Count:
Approach 1: 20
Approach 2: 18
The first approach managed to shatter the network into more pieces.
Average Connected Component Size:
Final Average Connected Component Size:
Approach 1: 1.65
Approach 2: 1.83
The first approach managed to shatter the network into smaller pieces.
In conclusion, in this network, the iterative approach caused greater disruption than the burst approach. With the first approach, resulting groups are smaller.
Offense and Defense
This is offense and defense. This is a more serious topic, but a fun game nonetheless. Because I know that nodes with high betweenness centrality hold networks together, I knew that eliminating them would shatter the network into pieces. This is network thinking.
In contrast, it would be much less effective to just work off of a list and hope for the best. The more context you have, the more effective you can be, in offense, defense, or anything.
With these networks, we can imagine different outcomes. We can simulate different approaches and ideas.
How’d We Do?
Before ending, let’s take a final look at the resulting disruptiveness of the first approach.
Before:
After:
Yup, that’s busted.
That’s All, Folks!
That’s all for today! Thanks for reading! If you would like to learn more about networks and network analysis, please buy a copy of my book!











I love that!
Your discussion of thinking in networks reminded me of the following quote from a sci-fi story published in 1952, emphasizing thinking in networks as a human quality as opposed to other species thinking sequentially.
The context is - Lavon, a microscopic human navigating the first ever watership (analogous to a spaceship) up a slope together with several other microscopic organism on a journey to the edge of the water:
"“A little more work from your diatoms, Tanol,” Lavon said. “Boulder ahead.” The ship swung ponderously. “All right, slow them up again. Give us a shove from your side, Tol—no, that’s too much—there, that’s it. Back to normal; you’re still turning us! Tanol, give us one burst to line us up again. Good. All right, steady drive on all sides. It shouldn’t be long now.”
“How can you think in webs like that?” the Para wondered behind him.
“I just do, that’s all. It’s the way men think. Overseers, a little more thrust now; the grade’s getting steeper.”
This was taken from "Surface Tension" by Anthony Blish:
https://en.wikipedia.org/wiki/Surface_Tension_(short_story)